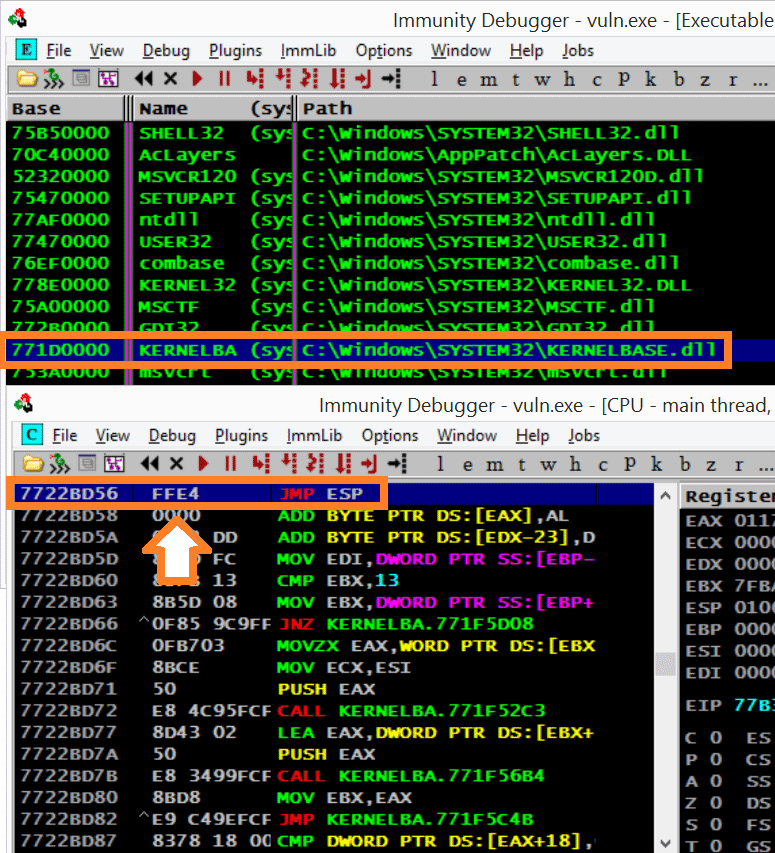
SUNY at Buffalo; Computer Science; CSE620 – Advanced Networking Concepts; Fall 2005; Instructor: Hung Q. Ngo 1 Agenda Last time: finished brief overview. - ppt download

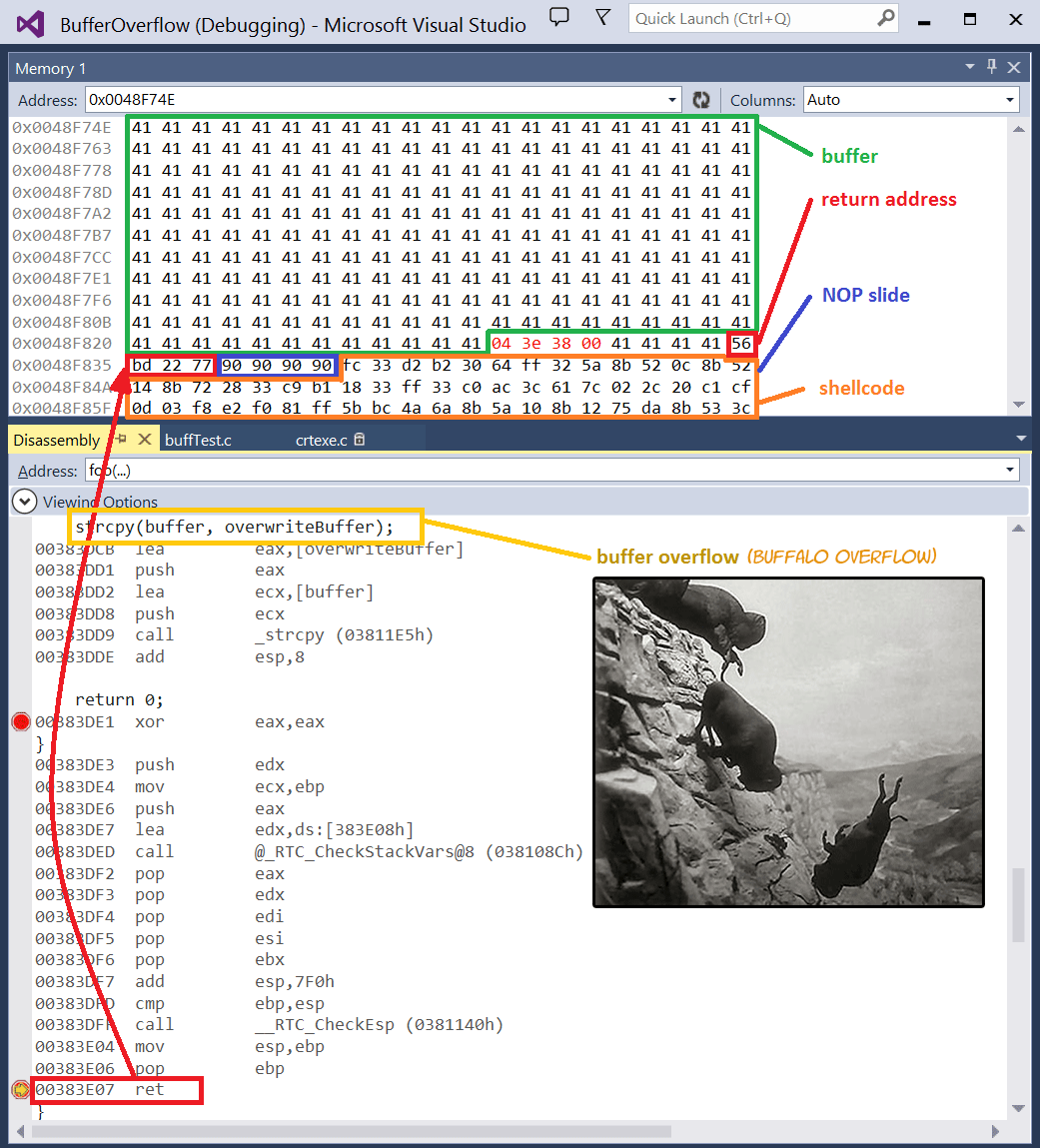
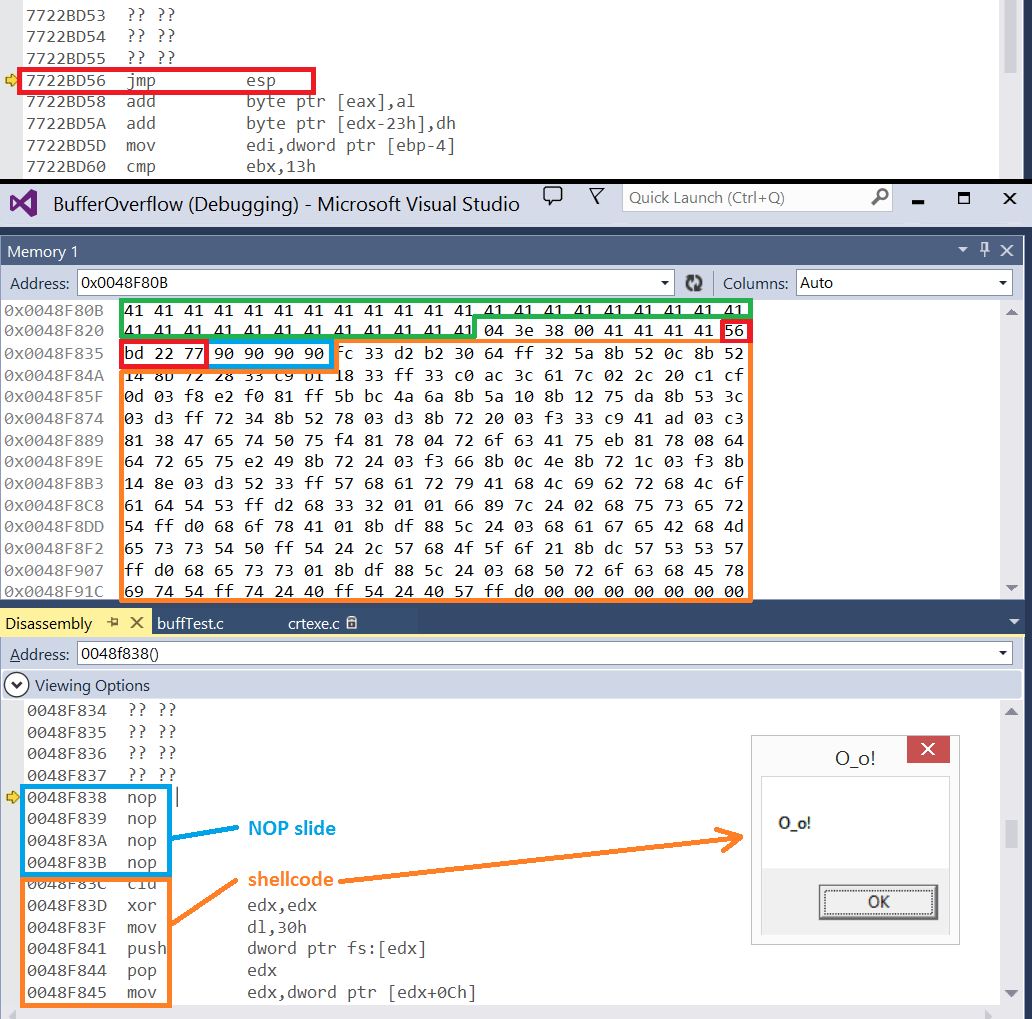
An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs

An introduction to computer buffer overflow problem on using unsecured C or C++ standard functions in C programs

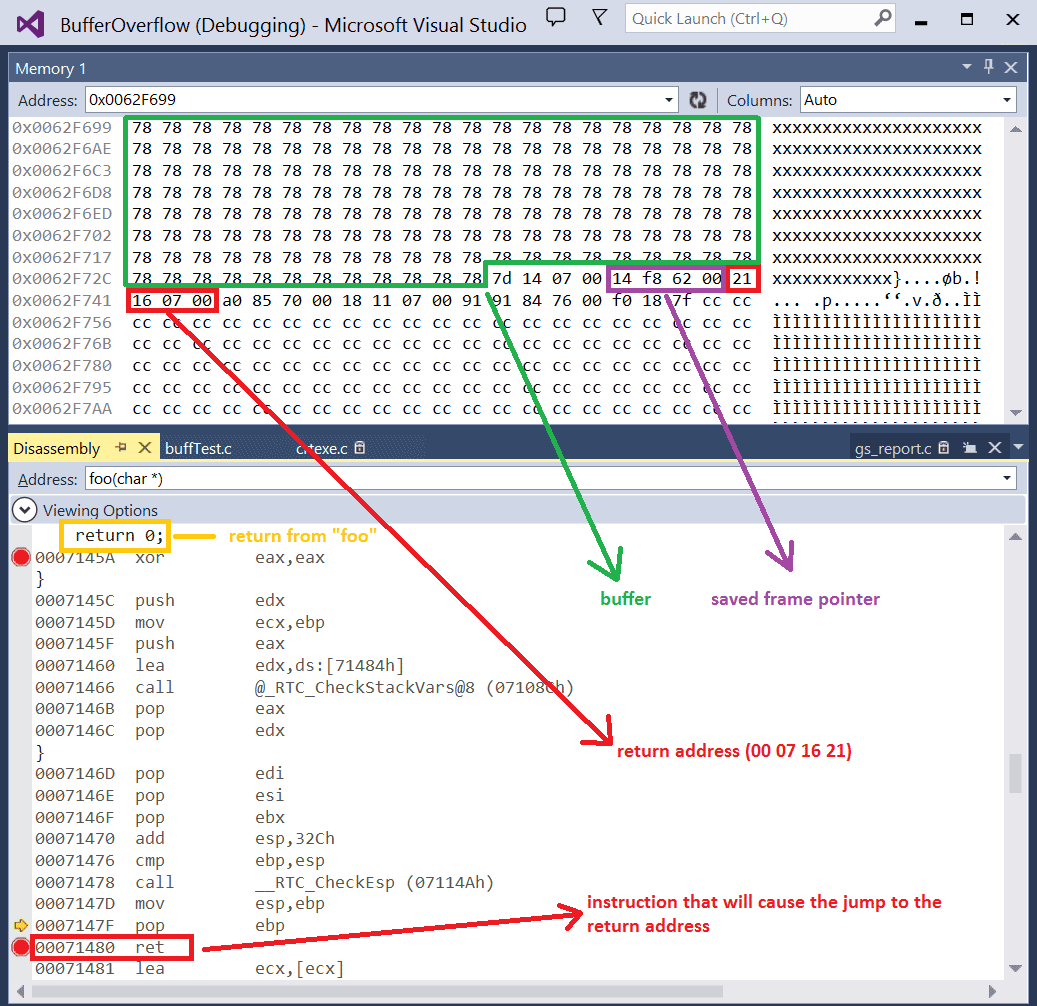
Buffer Overflow Lab.docx - Buffer Overflow Lab Based heavily on a lab developed by Wenliang Du of Syracuse University as part of the SEED labs series | Course Hero